Arm Announces a New Security Certification Program for IoT Devices
Last year Arm detailed their vision of a trillion connected devices and the Neoverse platform that is designed to enable it. Over the past month, we have seen some significant progress on the server side with the announcement of the Neoverse N1 and E1 platforms. Those platforms are designed to enable next-generation of Arm-based SoCs for anywhere from the edge and 5G base stations to networking and hyperscalers data centers. Today’s announcement focuses on the IoT aspect of their vision.
PSA
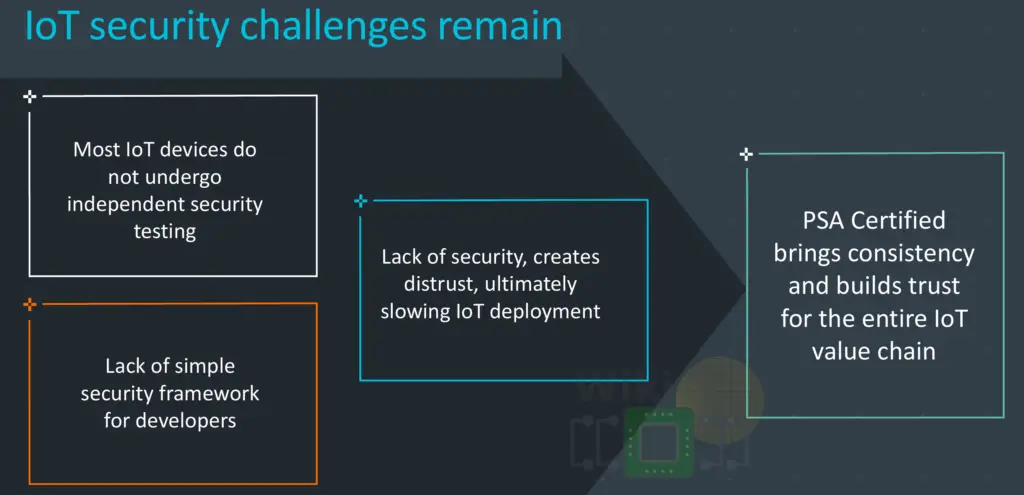
In late 2017 Arm introduced the Platform Security Architecture (PSA). PSA is an architecture-agnostic framework for streamlining security in IoT devices using a consistent and simple standard. The threat models, references models, and specifications are all freely published on the Arm website. Although it gained wide industry support, Arm claims that very few IoT devices are subjected to any security testing and an extremely tiny portion of that actually undergo independent security testing. Arm says that the lack of access to simple and consistent frameworks are slowing IoT deployment and market growth.
PSA Certified
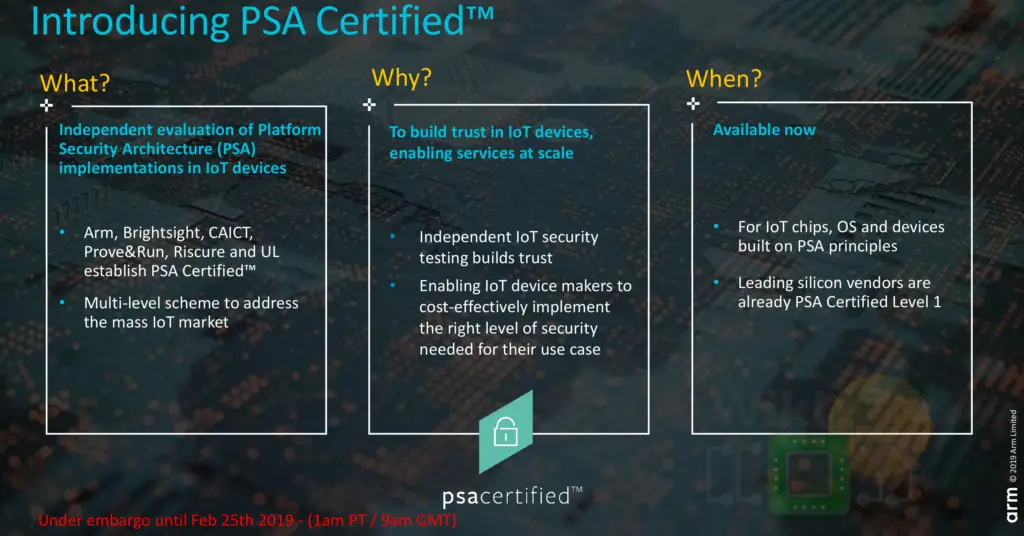
Today, Arm is announcing the PSA Certified program, a new and independent certification program for IoT devices that implement the platform security architecture. The certification is being introduced in order to ease the development of secure by design based on the desired level of security expected from the final product, enabling scaled deployment of trusted IoT. In other words, PSA Certified allow companies to independently verify that they meet the right level of security for their use case.
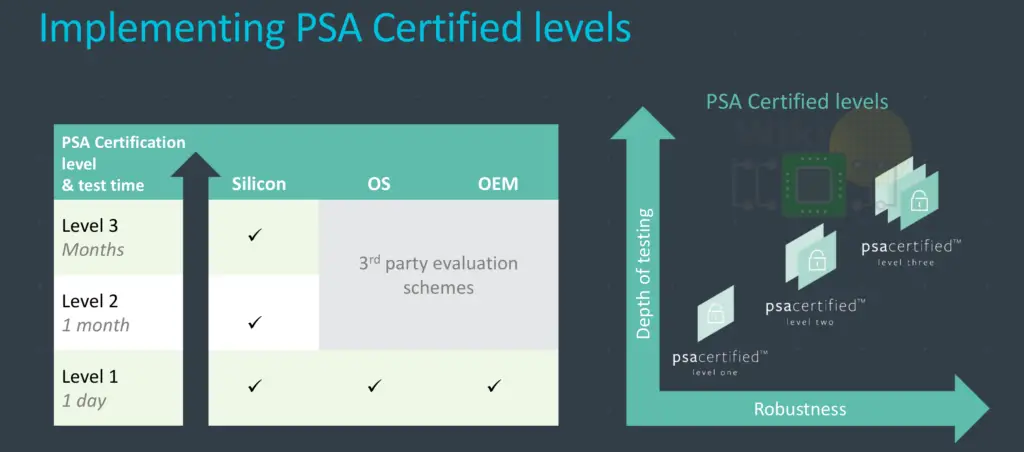
The PSA Certified program consists of two parts: a PSA functional API certification and an assurance and robustness certification based on progress levels of assurance (1 being the minimum level of security). The API Certification is designed to ensure that all chips properly follow a common API in order to offer better software interoperability, independent of hardware. Arm says that the PSA Certified program is already available today and is leveraged by OS vendors, silicon vendors, and OEMs with a number of silicon vendors already PSA level 1 certified.
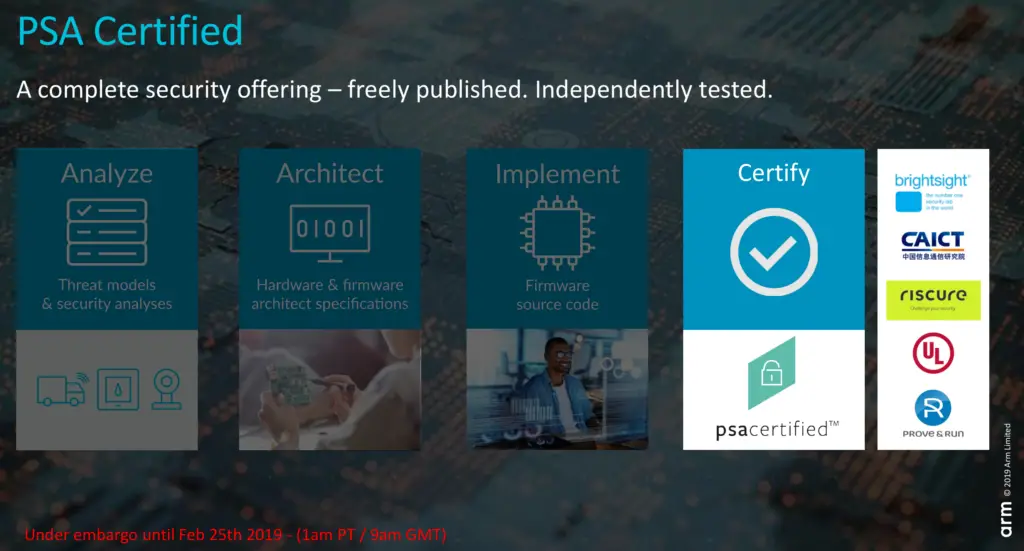
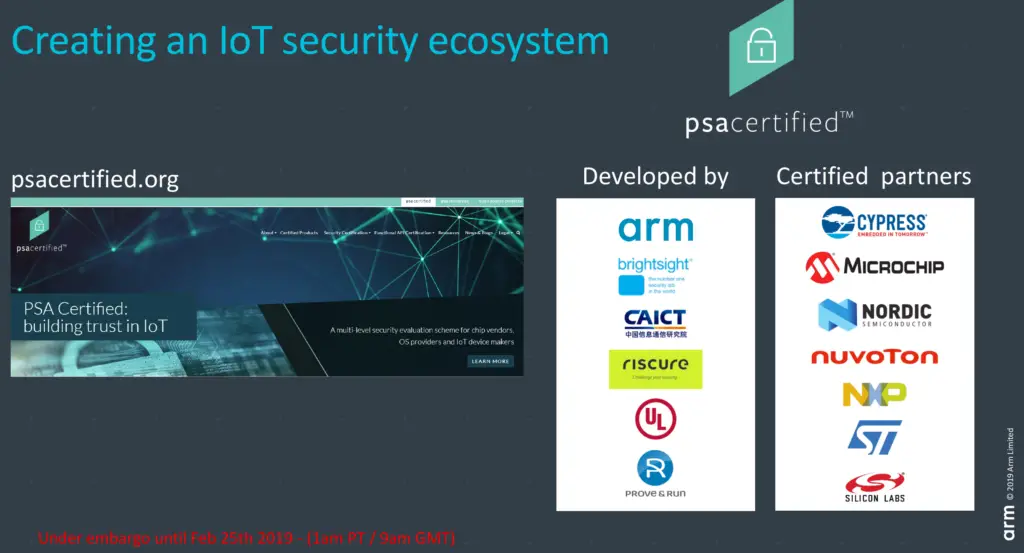
Arm has partnered with a number of major test labs in order to ensure the broadest possible enablement of PSA certifications. Those include Brightsight, CAICT, Prove&Run, Riscure, and UL.
It’s worth noting that the certification process can be done retroactively on chips that are already in the field. In this case, an identical chip will need to go through the appropriate levels of certifications and pass to be certified.
Assurance and Robustness Levels
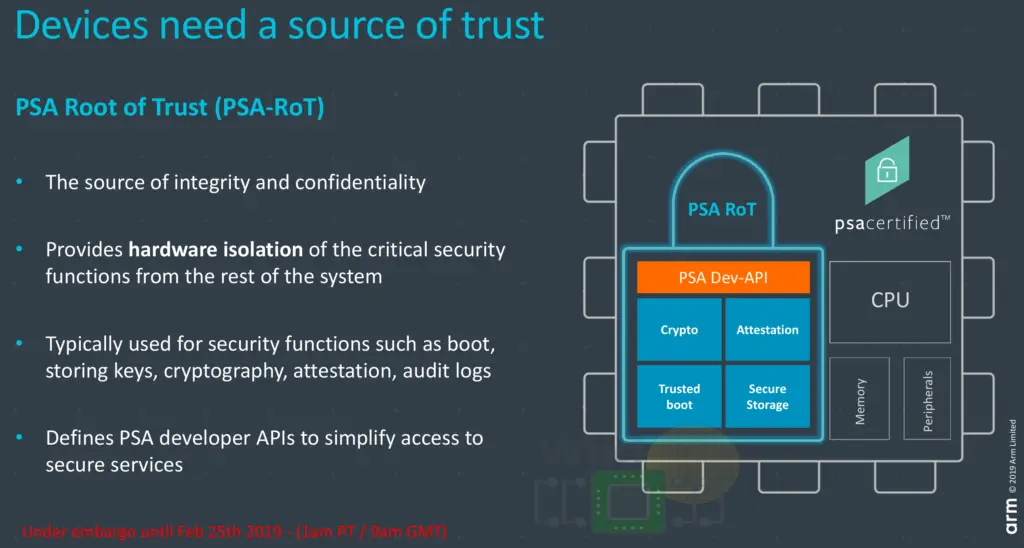
Like all secure IoT devices, at the at the heart of the platform security architecture is the specification for the PSA root of trust (PSA-RoT) which incorporates a number of essential security services such as secure storage, crypto, attestation, and secure boot. The PSA does sugar-coat those services with a nice interface to the OS designed to simplify the access to those services.
There are three PSA Certified levels based on the PSA-RoT, each one is progressively stricter in terms of assurance and robustness. Assurance, in this case, talks about the depth of testing involved while robustness refers to the scope and extent of the protections against various threats. Someone like a silicon vendor can start with a level 1 certification and if needed go into a month-long evaluation of controlled pen testing. If further required, they can go to level 3 which is much more exhaustive.
The three levels of assurance and robustness designed try to match the security needs of use cases with the correct level of security implemented in the IoT device. Arm gave a few example use cases. Consider temperature sensors being used in an agricultural environment, a home environment, and an industrial manufacturing environment. Though instinctively you’d think that the temperature sensor at the manufacturing plant requires the highest level of security assurance while the home and agricultural could use the lowest level. In practice, the highest level of security might be desired at the temperature sensor in the agricultural environment which might be part of an irrigation system which closely monitors and controls the crops. In this scenario, the security of the device and the trust in the data being generated from it is by far the most critical component of the three examples. Here, the highest level of security is required as an attack on that sensor could potentially result in the loss of the crops.
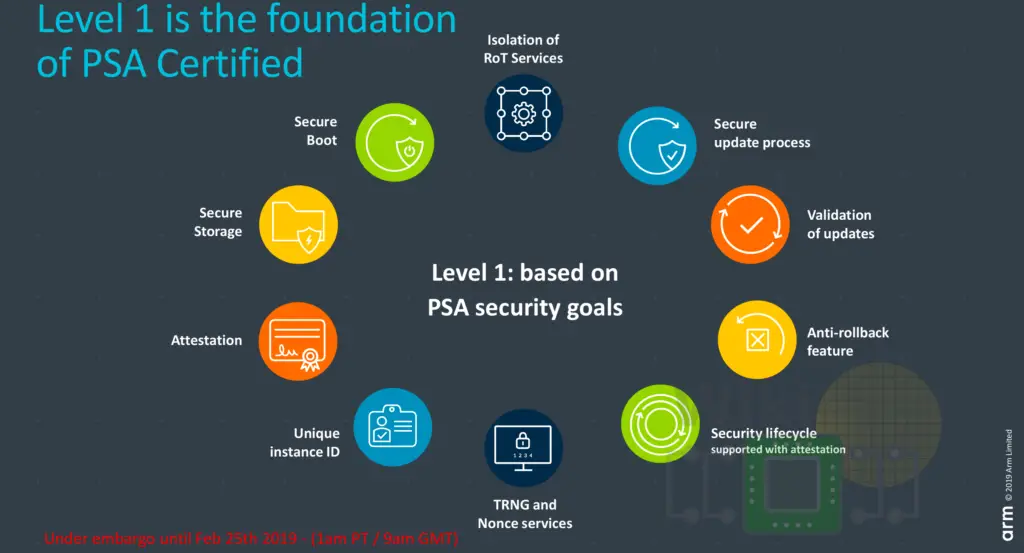
Level 1 is the minimum level of assurance and robustness. This is a review process involving a moderated questioner which must be backed by significant evidence that shows the implementation adheres to the various requirements. It is designed to make sure that the chip meets the basic goals of the platform security architecture. This includes ten foundational security features that they expect every device to have such attestation, secure storage, secure boot, and unique instance IDs. They also require devices to having security lifecycle states (ownership changes, debug), doing secure updates, validating those updates, anti-rollback capabilities. As part of the level 1 certification, Arm included a basic IoT threat model and industry best-practice policy. There are already a number of silicon partners with products achieving level 1 certification, including Cypress, Express Logic, Microchip, Nordic Semiconductor, Nuvoton, NXP, STMicroelectronics, and Silicon Labs.
Level 2 moves to a test lab evaluation time-bound testing of 1 month. Here you move from a review process to actual penetration testing of real silicon. This includes source code review and an agreed set of attack methods and evaluation methodology. All in all, the level 2 certification aims at mid-level assurance and robustness guarantees. Level 2 certification is also already available today. Level 3 is not currently available but will be delivered later this year. It includes a much longer period of time in the lab for higher assurance and incorporates more extensive attacks such as side channel and tamper.
–
Spotted an error? Help us fix it! Simply select the problematic text and press Ctrl+Enter to notify us.
–